f0cc5b953bf39e70ddfc52e25dff14b031f4341f
AI-IOT/.gitkeep
Automative/.gitkeep
BAP-WIKI-Cheat-Sheet.md
| ... | ... | @@ -0,0 +1,112 @@ |
| 1 | +--- |
|
| 2 | +title: BAP WIKI Cheat Sheet - Some of Gollum's features |
|
| 3 | +--- |
|
| 4 | + |
|
| 5 | +Some of Gollum's features. Based on the 5.x release. |
|
| 6 | + |
|
| 7 | +1. [General functions](#general) |
|
| 8 | +1. [Emojis](#emojis) |
|
| 9 | +1. [Citations](#citations) |
|
| 10 | +1. [Math](#math) |
|
| 11 | +1. [CriticMarkup Annotations](#criticmarkup) |
|
| 12 | +1. [Right To Left Languages](#right-to-left-languages) |
|
| 13 | +1. [Numbered Headings](#numbered-headings) |
|
| 14 | + |
|
| 15 | +# General |
|
| 16 | + |
|
| 17 | +### Viewing and Editing Pages, GlobalTOC Macro |
|
| 18 | + |
|
| 19 | + |
|
| 20 | + |
|
| 21 | +### Overview, History, Latest Changes, Compare Views |
|
| 22 | + |
|
| 23 | + |
|
| 24 | + |
|
| 25 | +# Emojis |
|
| 26 | + |
|
| 27 | +## Screenshot |
|
| 28 | + |
|
| 29 | + |
|
| 30 | + |
|
| 31 | +# Citations |
|
| 32 | + |
|
| 33 | +## Screenshot |
|
| 34 | + |
|
| 35 | + |
|
| 36 | + |
|
| 37 | +## Markup for achieving the above result for citations |
|
| 38 | + |
|
| 39 | +```markdown |
|
| 40 | +--- |
|
| 41 | +bibliography: zettel.bib |
|
| 42 | +csl: ieee.csl |
|
| 43 | +nocite: | |
|
| 44 | + |
|
| 45 | +--- |
|
| 46 | + |
|
| 47 | +# WFDB Record |
|
| 48 | + |
|
| 49 | +> **Date:** Tue 10 Mar 2020 06:15:25 AM UTC |
|
| 50 | +> |
|
| 51 | +> **Summary:** Overview of the Waveform Database (WFDB) record format |
|
| 52 | +> |
|
| 53 | +> **Keywords:** ##summary #wfdb #dataformat #storage #healthcare #opensource #standard |
|
| 54 | + |
|
| 55 | +## **Note Linked To:** |
|
| 56 | + |
|
| 57 | +### [The Technology Index](03162020223918-technology-index) |
|
| 58 | +- **Summary:** This index is a compilation of utilities and resources when working with any sort of technology. |
|
| 59 | + |
|
| 60 | +--- |
|
| 61 | + |
|
| 62 | +## **Overview:** |
|
| 63 | + |
|
| 64 | +The Waveform Database (WFDB) Library is a record management system to handle already existing databases - it itself is not a database but a collection of tools to handle databases that follow the WFDB format. [@moodyWFDBProgrammerGuide2019] Furthermore, WFDB can be used for viewing, analyzing, and creating recordings of physiological signals [@garciamartinezLoadingPlottingFiltering2017]. |
|
| 65 | + |
|
| 66 | +## **How It Works:** |
|
| 67 | + |
|
| 68 | +The way that the WFDB record format works is that it utilizes [@moodyWFDBProgrammerGuide2019]: |
|
| 69 | + |
|
| 70 | +- **Header Files** to specify the characteristics of a signal (sampling frequency, etc.) |
|
| 71 | +- **Annotation Files** to record annotations corresponding to a signal (generally kept in time with the rest of the signal) |
|
| 72 | + |
|
| 73 | +## **Example Application - ECG Data:** |
|
| 74 | + |
|
| 75 | +For example, when working with ECG data, the format utilizes the header and annotation files as follows [@moodyWFDBProgrammerGuide2019]: |
|
| 76 | + |
|
| 77 | +- **Header Files** - could contain information about lead count, calibration format, etc. |
|
| 78 | +- **Annotation Files** - could contain other information such as beat positions. |
|
| 79 | + |
|
| 80 | +## **Miscellaneous Notes:** |
|
| 81 | + |
|
| 82 | +- WFDB is considered a standard data format within the research world, and has found application in industry as well. |
|
| 83 | +- The WFDB format is generally used for ECG records - however, it can extend to other data formats. |
|
| 84 | +- A possible alternative to the WFDB record format is the European Data Format+ (EDF+) [@garciamartinezLoadingPlottingFiltering2017]. |
|
| 85 | + |
|
| 86 | +### **References:** |
|
| 87 | + |
|
| 88 | +``` |
|
| 89 | + |
|
| 90 | +# Math |
|
| 91 | + |
|
| 92 | + |
|
| 93 | + |
|
| 94 | +# CriticMarkup |
|
| 95 | + |
|
| 96 | +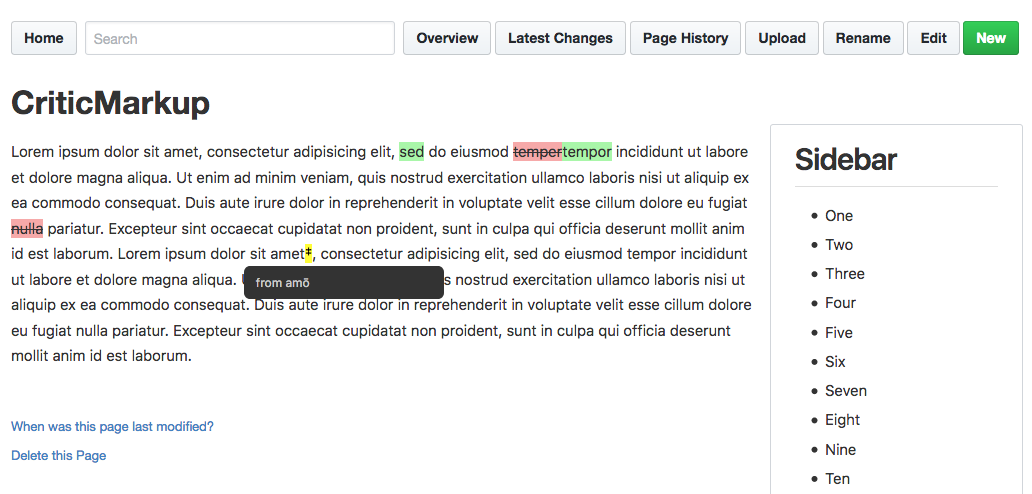 |
|
| 97 | + |
|
| 98 | +# Right To Left Languages |
|
| 99 | + |
|
| 100 | + |
|
| 101 | + |
|
| 102 | +# Numbered Headings |
|
| 103 | + |
|
| 104 | +See [here](Home#enabling-header-counting). |
|
| 105 | + |
|
| 106 | +## Roman |
|
| 107 | + |
|
| 108 | +<img width="722" alt="screen shot 2018-10-15 at 01 19 42" src="https://user-images.githubusercontent.com/147111/46923576-d4568580-d019-11e8-9441-257edc3bfe8c.png"> |
|
| 109 | + |
|
| 110 | +## Tibetan |
|
| 111 | + |
|
| 112 | +<img width="696" alt="screen shot 2018-10-15 at 01 19 28" src="https://user-images.githubusercontent.com/147111/46923578-e1737480-d019-11e8-95dc-c28416423082.png"> |
Blockchain/.gitkeep
Digital Transformation/.gitkeep
E-Commerce/.gitkeep
Finance & Securities/.gitkeep
Game 2D&3D/.gitkeep
Home.md
| ... | ... | @@ -1,3 +1,23 @@ |
| 1 | 1 | # WELCOME TO BAP WIKI |
| 2 | 2 | |
| 3 | -<<GlobalTOC()>> |
|
| ... | ... | \ No newline at end of file |
| 0 | + |
|
| 1 | +Chào mừng bạn đến với BAP WIKI |
|
| 2 | + |
|
| 3 | +**BAP WIKI** sử dụng Gollum kết hợp GitLab giúp việc đóng góp trở nên đơn giản hơn bao giờ hết, mọi người có thể viết bài bằng Markdown và tạo merge request |
|
| 4 | + |
|
| 5 | + |
|
| 6 | +**BAP WIKI** là điễn đàn mở cho cộng đồng BAPER có thể chia sẻ và đóng góp kiến thức của mình một cách dễ dàng. |
|
| 7 | + |
|
| 8 | +### Cách đóng góp: |
|
| 9 | +- Tạo bài viết vào thư mục tương ứng với Business Domain, tham khảo syntax tại [[BAP-WIKI-Cheat-Sheet.md]] |
|
| 10 | +- Tạo merge request vào nhánh master |
|
| 11 | + |
|
| 12 | +Hãy cùng đóng góp và chia sẻ kiến thức của bạn tại BAP WIKI, nơi mà sự đa dạng và tích lũy kiến thức là chìa khóa cho sự phát triển của cộng đồng BAP và các lĩnh vực liên quan. |
|
| 13 | + |
|
| 14 | +<<GlobalTOC("Danh sách toàn bộ các bài viết")>> |
|
| 15 | + |
|
| 16 | + |
|
| 17 | + |
|
| 18 | +---- |
|
| 19 | + |
|
| 20 | +> |
Mobile Utility/.gitkeep
Quality Assurance/sonarqube/.gitkeep
Quality Assurance/sonarqube/SonarQube-how-to-run-analysis-on-your-project.md
| ... | ... | @@ -0,0 +1,385 @@ |
| 1 | + |
|
| 2 | +[TOC] |
|
| 3 | + |
|
| 4 | +[[_TOC_]] |
|
| 5 | + |
|
| 6 | +## 1. Provide a token |
|
| 7 | + |
|
| 8 | +https://sonar.bappartners.com/account/security |
|
| 9 | + |
|
| 10 | +- If you have the right to run the analysis code and publish it to the SonarQube server |
|
| 11 | +please create a token here https://sonar.bappartners.com/account/security. |
|
| 12 | + |
|
| 13 | +- If you do not have permission to run the analysis, please contact the administrator (thachpv) to obtain a token. |
|
| 14 | + |
|
| 15 | +## 2. Run analysis on your project |
|
| 16 | + |
|
| 17 | +### Analysis parameters |
|
| 18 | + |
|
| 19 | + |
|
| 20 | + |
|
| 21 | +- Some analysis parameters |
|
| 22 | + |
|
| 23 | +| Parameters | Description | |
|
| 24 | +| ----------- | ----------- | |
|
| 25 | +| `sonar.token` | Token used by the scanner to authenticate to the SonarCloud server. <br />Replaces `sonar.login` and `sonar.password` properties which are deprecated. | |
|
| 26 | +| `sonar.host.url` | https://sonar.bappartners.com/ . The URL of the SonarCloud server | |
|
| 27 | +| `sonar.projectKey` | The project's unique key. Example format: `s0027.ChallengeCR_tên_repo`| |
|
| 28 | +| `sonar.projectName` | Name of the project that will be displayed on the web interface. Example format: `s0027.ChallengeCR_tên_repo`| |
|
| 29 | +| `sonar.sources` | Analysis baseline for main source code (non-test code) in the project.| |
|
| 30 | +| `sonar.tests` | Analysis baseline for test code in the project.| |
|
| 31 | +| `sonar.sourceEncoding` | Encoding of the source files. For example, `UTF-8`, `MacRoman`, `Shift_JIS`. The list of available encodings depends on your JVM.| |
|
| 32 | +| `sonar.exclusions` | A setting used to specify file paths that you want to exclude from the SonarQube analysis process | |
|
| 33 | + |
|
| 34 | + Please visit the [official documentation of Analysis parameters](https://docs.sonarsource.com/sonarcloud/advanced-setup/analysis-parameters/) for more details. |
|
| 35 | + |
|
| 36 | + |
|
| 37 | +- Setting configuration in a file |
|
| 38 | + - Maven Java project: `pom.xml` |
|
| 39 | + - Gradle Java project: `build.gradle` |
|
| 40 | + - Ant Java project: `build.xml` |
|
| 41 | + - Other CI-based analysis: `sonar-project.properties` |
|
| 42 | + - Automatic analysis: `.sonarcloud.properties` |
|
| 43 | + |
|
| 44 | +- Setting configuration on the command line |
|
| 45 | + - For CI-based analysis (not automatic analysis), parameters can also be set on the command line using the `-D` option indicator when launching an analysis |
|
| 46 | + |
|
| 47 | +### Execute the Scanner for Maven |
|
| 48 | + Running a SonarQube analysis with Maven is straighforward. You just need to run the following command in your project's folder. |
|
| 49 | + |
|
| 50 | + ```bash |
|
| 51 | + mvn clean verify sonar:sonar \ |
|
| 52 | + -Dsonar.projectKey=test1 \ |
|
| 53 | + -Dsonar.host.url=https://sonar.bappartners.com \ |
|
| 54 | + -Dsonar.login=sqp_a8f356df86c4c1660db14aa849bc1a829aaa3e42 |
|
| 55 | + ``` |
|
| 56 | + |
|
| 57 | + Please visit the [official documentation of the Scanner for Maven](https://docs.sonarsource.com/sonarqube/9.9/analyzing-source-code/scanners/sonarscanner-for-maven/) for more details. |
|
| 58 | + |
|
| 59 | +### Execute the Scanner for Gradle |
|
| 60 | + |
|
| 61 | +1/ Running an analysis with Gradle is straighforward. You just need to declare the `org.sonarqube` plugin in your `build.gradle` file: |
|
| 62 | + |
|
| 63 | +``` |
|
| 64 | +plugins { |
|
| 65 | + id "org.sonarqube" version "3.5.0.2730" |
|
| 66 | +} |
|
| 67 | +``` |
|
| 68 | + |
|
| 69 | +2/ run the following command: |
|
| 70 | + |
|
| 71 | +```bash |
|
| 72 | +./gradlew sonar \ |
|
| 73 | + -Dsonar.projectKey=test1 \ |
|
| 74 | + -Dsonar.host.url=https://sonar.bappartners.com \ |
|
| 75 | + -Dsonar.login=sqp_a8f356df86c4c1660db14aa849bc1a829aaa3e42 |
|
| 76 | +``` |
|
| 77 | + |
|
| 78 | +### Other (for JS, TS, Go, Python, PHP, ...) |
|
| 79 | +1/ Download and unzip the Scanner for Linux |
|
| 80 | + |
|
| 81 | +- https://docs.sonarsource.com/sonarcloud/advanced-setup/ci-based-analysis/sonarscanner-cli/ |
|
| 82 | + |
|
| 83 | +2/ Execute the Scanner |
|
| 84 | + |
|
| 85 | +```bash |
|
| 86 | +sonar-scanner \ |
|
| 87 | + -Dsonar.projectKey=test1 \ |
|
| 88 | + -Dsonar.sources=. \ |
|
| 89 | + -Dsonar.host.url=https://sonar.bappartners.com \ |
|
| 90 | + -Dsonar.login=sqp_a8f356df86c4c1660db14aa849bc1a829aaa3e42 |
|
| 91 | +``` |
|
| 92 | + |
|
| 93 | +Please visit the [official documentation of the Scanner](https://docs.sonarsource.com/sonarqube/9.9/analyzing-source-code/scanners/sonarscanner/) for more details. |
|
| 94 | + |
|
| 95 | +### Scanner .NET Core Global Tool |
|
| 96 | + |
|
| 97 | +``` |
|
| 98 | +dotnet tool install --global dotnet-sonarscanner |
|
| 99 | +``` |
|
| 100 | + |
|
| 101 | +``` |
|
| 102 | +dotnet sonarscanner begin /k:"test1" /d:sonar.host.url="https://sonar.bappartners.com" /d:sonar.login="sqp_a8f356df86c4c1660db14aa849bc1a829aaa3e42" |
|
| 103 | +dotnet build |
|
| 104 | +dotnet sonarscanner end /d:sonar.login="sqp_a8f356df86c4c1660db14aa849bc1a829aaa3e42" |
|
| 105 | +``` |
|
| 106 | + |
|
| 107 | +### Execute the Scanner for Flutter |
|
| 108 | + |
|
| 109 | +- Sonar Server need to install SonarQube plugin for Flutter/Dart: https://github.com/insideapp-oss/sonar-flutter |
|
| 110 | + |
|
| 111 | +- Create `sonar-project.properties` file |
|
| 112 | +``` |
|
| 113 | +# Project identification |
|
| 114 | +sonar.projectKey=tcu.knock-fe-user |
|
| 115 | +sonar.projectVersion=1.0 |
|
| 116 | +sonar.host.url=http://localhost:9000 |
|
| 117 | +sonar.login=sqp_aae237585c0c1995591c82faae02c619eae1dc94 |
|
| 118 | + |
|
| 119 | +# Source code location. |
|
| 120 | +# Path is relative to the sonar-project.properties file. Defaults to . |
|
| 121 | +# Use commas to specify more than one file/folder. |
|
| 122 | +# It is good practice to add pubspec.yaml to the sources as the analyzer |
|
| 123 | +# may produce warnings for this file as well. |
|
| 124 | +sonar.sources=lib,pubspec.yaml |
|
| 125 | +#sonar.tests=test |
|
| 126 | + |
|
| 127 | +# Encoding of the source code. Default is default system encoding. |
|
| 128 | +sonar.sourceEncoding=UTF-8 |
|
| 129 | + |
|
| 130 | +# Analyzer mode |
|
| 131 | +# Can be: |
|
| 132 | +# - DETECT (attempt to detect automatically) - default |
|
| 133 | +# - MANUAL (an existing report needs to be provided) |
|
| 134 | +# - FLUTTER (flutter analyze) |
|
| 135 | +# - DART (dart analyze) |
|
| 136 | +# - DARTANALYZER (dartanalyzer) |
|
| 137 | +# sonar.dart.analyzer.mode= |
|
| 138 | + |
|
| 139 | +# Allows reuse of an existing analyzer report when mode is MANUAL |
|
| 140 | +# sonar.dart.analyzer.report.path= |
|
| 141 | + |
|
| 142 | +# Analyzer report output mode |
|
| 143 | +# Can be: |
|
| 144 | +# - DETECT (attempt to detect automatically, requires Dart SDK on the PATH) - default |
|
| 145 | +# - MACHINE (a new machine readable output that is available for Dart 2.12+) |
|
| 146 | +# - LEGACY (attempts to parse human readable output from dart/flutter) - default |
|
| 147 | +# sonar.dart.analyzer.report.mode= |
|
| 148 | +``` |
|
| 149 | + |
|
| 150 | +- Run the analysis and publish to the SonarQube server |
|
| 151 | +```bash |
|
| 152 | +# Download dependencies |
|
| 153 | +flutter pub get |
|
| 154 | +# Run tests with User feedback (in case some test are failing) |
|
| 155 | +#flutter test |
|
| 156 | +# Run tests without user feedback regeneration tests.output and coverage/lcov.info |
|
| 157 | +#flutter test --machine --coverage > tests.output |
|
| 158 | + |
|
| 159 | +# Run the analysis and publish to the SonarQube server |
|
| 160 | +sonar-scanner |
|
| 161 | +``` |
|
| 162 | +---- |
|
| 163 | + |
|
| 164 | +## Analyze your project with GitLab CI |
|
| 165 | +### MAVEN |
|
| 166 | + |
|
| 167 | +**1/ Add the following to your `pom.xml` file** |
|
| 168 | +``` |
|
| 169 | +<properties> |
|
| 170 | + <sonar.qualitygate.wait>true</sonar.qualitygate.wait> |
|
| 171 | +</properties> |
|
| 172 | +``` |
|
| 173 | + |
|
| 174 | + |
|
| 175 | +**2/ Add environment variables** |
|
| 176 | + |
|
| 177 | +2.1/ Define the SonarQube Token environment variable. |
|
| 178 | + |
|
| 179 | +- In GitLab, go to `Settings > CI/CD > Variables` to add the following variable and make sure it is available for your project: |
|
| 180 | +- In the Key field, enter `SONAR_TOKEN` |
|
| 181 | +- In the Value field, enter an existing token, or a newly generated one: [Generate a token](https://sonar.bappartners.com/account/security) |
|
| 182 | +- Uncheck the Protect Variable checkbox. |
|
| 183 | +- Check the Mask Variable checkbox. |
|
| 184 | + |
|
| 185 | +2.2/Define the SonarQube URL environment variable. |
|
| 186 | + |
|
| 187 | +Still in `Settings > CI/CD > Variables` add a new variable and make sure it is available for your project: |
|
| 188 | +- In the Key field, enter `SONAR_HOST_URL` |
|
| 189 | +- In the Value field, enter https://sonar.bappartners.com |
|
| 190 | +- Uncheck the Protect Variable checkbox. |
|
| 191 | +- Leave the Mask Variable checkbox unchecked. |
|
| 192 | + |
|
| 193 | + |
|
| 194 | +3/Create or update your `.gitlab-ci.yml` file with the following content. |
|
| 195 | + |
|
| 196 | +``` |
|
| 197 | +stages: |
|
| 198 | + - analyze |
|
| 199 | +sonarqube-check: |
|
| 200 | + stage: analyze |
|
| 201 | + image: maven:3.6.3-jdk-11 |
|
| 202 | + variables: |
|
| 203 | + SONAR_USER_HOME: "${CI_PROJECT_DIR}/.sonar" # Defines the location of the analysis task cache |
|
| 204 | + GIT_DEPTH: "0" # Tells git to fetch all the branches of the project, required by the analysis task |
|
| 205 | + cache: |
|
| 206 | + key: "${CI_JOB_NAME}" |
|
| 207 | + paths: |
|
| 208 | + - .sonar/cache |
|
| 209 | + script: |
|
| 210 | + - mvn verify sonar:sonar -Dsonar.projectKey=test1 |
|
| 211 | + rules: |
|
| 212 | + - if: $CI_PIPELINE_SOURCE == "merge_request_event" |
|
| 213 | + when: manual |
|
| 214 | + - if: '$CI_PIPELINE_SOURCE == "schedule" && $CI_COMMIT_BRANCH == "develop"' |
|
| 215 | + allow_failure: true |
|
| 216 | + tags: |
|
| 217 | + - sonar-scanner |
|
| 218 | +``` |
|
| 219 | + |
|
| 220 | +### gradle |
|
| 221 | + |
|
| 222 | +1/ Add the following to your `build.gradle` file |
|
| 223 | + |
|
| 224 | +``` |
|
| 225 | +plugins { |
|
| 226 | + id "org.sonarqube" version "3.5.0.2730" |
|
| 227 | +} |
|
| 228 | + |
|
| 229 | +sonar { |
|
| 230 | + properties { |
|
| 231 | + property "sonar.projectKey", "test1" |
|
| 232 | + property "sonar.qualitygate.wait", true |
|
| 233 | + } |
|
| 234 | +} |
|
| 235 | +``` |
|
| 236 | + |
|
| 237 | +Example: |
|
| 238 | +``` |
|
| 239 | +// SonarQube |
|
| 240 | +sonar { |
|
| 241 | + properties { |
|
| 242 | + property 'sonar.sourceEncoding', 'UTF-8' |
|
| 243 | + property 'sonar.language', 'java' |
|
| 244 | + property 'sonar.java.binaries', '**/build/classes' |
|
| 245 | + property 'sonar.exclusions', '**/com/honda/rd/**,**/ext/preevisionadapter/**' |
|
| 246 | + property 'sonar.issue.ignore.allfile', 'e1' |
|
| 247 | + property 'sonar.issue.ignore.allfile.e1.fileRegexp', '@Test' |
|
| 248 | + property 'sonar.issue.ignore.allfile', 'e2' |
|
| 249 | + property 'sonar.issue.ignore.allfile.e2.fileRegexp', '@ParameterizedTest' |
|
| 250 | + property 'sonar.junit.reportPaths', 'build/test-results/aggregate' |
|
| 251 | + property 'sonar.coverage.jacoco.xmlReportPaths', 'build/reports/jacoco/aggregate/jacocoTestReport.xml' |
|
| 252 | + property 'sonar.coverage.exclusions', '**/src/test/**' |
|
| 253 | + property 'sonar.cpd.exclusions', '**/src/test/**' |
|
| 254 | + } |
|
| 255 | +} |
|
| 256 | +project.tasks['sonar'].dependsOn 'junit5TestReport' |
|
| 257 | +project.tasks['sonar'].dependsOn 'aggregateJacocoMerge' |
|
| 258 | +``` |
|
| 259 | + |
|
| 260 | +2/ Create or update your `.gitlab-ci.yml` file with the following content. |
|
| 261 | +``` |
|
| 262 | +stages: |
|
| 263 | + - analyze |
|
| 264 | +sonarqube-check: |
|
| 265 | + stage: analyze |
|
| 266 | + image: gradle:jre11-slim |
|
| 267 | + variables: |
|
| 268 | + SONAR_USER_HOME: "${CI_PROJECT_DIR}/.sonar" # Defines the location of the analysis task cache |
|
| 269 | + GIT_DEPTH: "0" # Tells git to fetch all the branches of the project, required by the analysis task |
|
| 270 | + cache: |
|
| 271 | + key: "${CI_JOB_NAME}" |
|
| 272 | + paths: |
|
| 273 | + - .sonar/cache |
|
| 274 | + script: gradle sonar |
|
| 275 | + rules: |
|
| 276 | + - if: $CI_PIPELINE_SOURCE == "merge_request_event" |
|
| 277 | + when: manual |
|
| 278 | + - if: '$CI_PIPELINE_SOURCE == "schedule" && $CI_COMMIT_BRANCH == "develop"' |
|
| 279 | + allow_failure: true |
|
| 280 | + tags: |
|
| 281 | + - sonar-scanner |
|
| 282 | +``` |
|
| 283 | + |
|
| 284 | +### Other (for JS, TS, Go, Python, PHP, ...) |
|
| 285 | + |
|
| 286 | +1/ Create a `sonar-project.properties` file in your repository and paste the following code |
|
| 287 | + |
|
| 288 | +``` |
|
| 289 | +# must be unique in a given SonarQube instance |
|
| 290 | +sonar.projectKey=s0168.Monocad_lambda-flask-api |
|
| 291 | +# --- optional properties --- |
|
| 292 | + |
|
| 293 | +# defaults to project key |
|
| 294 | +sonar.projectName=s0168.Monocad_lambda-flask-api |
|
| 295 | +# defaults to 'not provided' |
|
| 296 | +#sonar.projectVersion=1.0 |
|
| 297 | + |
|
| 298 | +# Path is relative to the sonar-project.properties file. Defaults to . |
|
| 299 | +# sonar.projectBaseDir=. |
|
| 300 | +# sonar.sources=./src,./resources,./web |
|
| 301 | +sonar.sources=./app |
|
| 302 | + |
|
| 303 | +# Encoding of the source code. Default is default system encoding |
|
| 304 | +sonar.sourceEncoding=UTF-8 |
|
| 305 | + |
|
| 306 | +#sonar.test.inclusions=**/*Test.js |
|
| 307 | + |
|
| 308 | +#sonar.exclusions=,**/coverage/** |
|
| 309 | + |
|
| 310 | +# Fail CI pipeline if Sonar fails. |
|
| 311 | +sonar.qualitygate.wait=true |
|
| 312 | +``` |
|
| 313 | + |
|
| 314 | +2/ Create or update your `.gitlab-ci.yml` file with the following content. |
|
| 315 | +``` |
|
| 316 | +stages: |
|
| 317 | + - analyze |
|
| 318 | +sonarqube-check: |
|
| 319 | + stage: analyze |
|
| 320 | + image: |
|
| 321 | + name: sonarsource/sonar-scanner-cli:4.8 |
|
| 322 | + entrypoint: [""] |
|
| 323 | + variables: |
|
| 324 | + SONAR_USER_HOME: "${CI_PROJECT_DIR}/.sonar" # Defines the location of the analysis task cache |
|
| 325 | + GIT_DEPTH: "0" # Tells git to fetch all the branches of the project, required by the analysis task |
|
| 326 | + cache: |
|
| 327 | + key: "${CI_JOB_NAME}" |
|
| 328 | + paths: |
|
| 329 | + - .sonar/cache |
|
| 330 | + script: |
|
| 331 | + - sonar-scanner |
|
| 332 | + rules: |
|
| 333 | + - if: $CI_PIPELINE_SOURCE == "merge_request_event" |
|
| 334 | + when: manual |
|
| 335 | + - if: $CI_PIPELINE_SOURCE == "schedule" && $CI_COMMIT_BRANCH == "develop" |
|
| 336 | + allow_failure: true |
|
| 337 | + tags: |
|
| 338 | + - sonar-scanner |
|
| 339 | +``` |
|
| 340 | + |
|
| 341 | +### NET |
|
| 342 | + |
|
| 343 | +**1/ Add environment variables** |
|
| 344 | + |
|
| 345 | +1.1/ Define the SonarQube Token environment variable. |
|
| 346 | + |
|
| 347 | +- In GitLab, go to `Settings > CI/CD > Variables` to add the following variable and make sure it is available for your project: |
|
| 348 | +- In the Key field, enter `SONAR_TOKEN` |
|
| 349 | +- In the Value field, enter an existing token, or a newly generated one: [Generate a token](https://sonar.bappartners.com/account/security) |
|
| 350 | +- Uncheck the Protect Variable checkbox. |
|
| 351 | +- Check the Mask Variable checkbox. |
|
| 352 | + |
|
| 353 | +1.2/Define the SonarQube URL environment variable. |
|
| 354 | + |
|
| 355 | +Still in `Settings > CI/CD > Variables` add a new variable and make sure it is available for your project: |
|
| 356 | +- In the Key field, enter `SONAR_HOST_URL` |
|
| 357 | +- In the Value field, enter https://sonar.bappartners.com |
|
| 358 | +- Uncheck the Protect Variable checkbox. |
|
| 359 | +- Leave the Mask Variable checkbox unchecked. |
|
| 360 | + |
|
| 361 | +2/ Create or update your `.gitlab-ci.yml` file with the following content. |
|
| 362 | +``` |
|
| 363 | +sonarqube-check: |
|
| 364 | + image: mcr.microsoft.com/dotnet/core/sdk:latest |
|
| 365 | + variables: |
|
| 366 | + SONAR_USER_HOME: "${CI_PROJECT_DIR}/.sonar" # Defines the location of the analysis task cache |
|
| 367 | + GIT_DEPTH: "0" # Tells git to fetch all the branches of the project, required by the analysis task |
|
| 368 | + cache: |
|
| 369 | + key: "${CI_JOB_NAME}" |
|
| 370 | + paths: |
|
| 371 | + - .sonar/cache |
|
| 372 | + script: |
|
| 373 | + - "apt-get update" |
|
| 374 | + - "apt-get install --yes openjdk-11-jre" |
|
| 375 | + - "dotnet tool install --global dotnet-sonarscanner" |
|
| 376 | + - "export PATH=\"$PATH:$HOME/.dotnet/tools\"" |
|
| 377 | + - "dotnet sonarscanner begin /k:\"s0202.meta.b2b.unity_fe\" /d:sonar.login=\"$SONAR_TOKEN\" /d:\"sonar.host.url=$SONAR_HOST_URL\" " |
|
| 378 | + - "dotnet build" |
|
| 379 | + - "dotnet sonarscanner end /d:sonar.login=\"$SONAR_TOKEN\"" |
|
| 380 | + allow_failure: true |
|
| 381 | + only: |
|
| 382 | + - merge_requests |
|
| 383 | + - staging |
|
| 384 | + - develop |
|
| 385 | +``` |
Quality Assurance/sonarqube/setting_hierachy.png
| ... | ... | Binary files /dev/null and b/Quality Assurance/sonarqube/setting_hierachy.png differ |
SAP/.gitkeep
TEST.md
| ... | ... | @@ -1,3 +0,0 @@ |
| 1 | ---- |
|
| 2 | -title: My Overriden Title |
|
| 3 | ---- |
|
| ... | ... | \ No newline at end of file |
Web Utility/.gitkeep
sonarqube/readme.md
| ... | ... | @@ -1,385 +0,0 @@ |
| 1 | - |
|
| 2 | -[TOC] |
|
| 3 | - |
|
| 4 | -[[_TOC_]] |
|
| 5 | - |
|
| 6 | -## 1. Provide a token |
|
| 7 | - |
|
| 8 | -https://sonar.bappartners.com/account/security |
|
| 9 | - |
|
| 10 | -- If you have the right to run the analysis code and publish it to the SonarQube server |
|
| 11 | -please create a token here https://sonar.bappartners.com/account/security. |
|
| 12 | - |
|
| 13 | -- If you do not have permission to run the analysis, please contact the administrator (thachpv) to obtain a token. |
|
| 14 | - |
|
| 15 | -## 2. Run analysis on your project |
|
| 16 | - |
|
| 17 | -### Analysis parameters |
|
| 18 | - |
|
| 19 | - |
|
| 20 | - |
|
| 21 | -- Some analysis parameters |
|
| 22 | - |
|
| 23 | -| Parameters | Description | |
|
| 24 | -| ----------- | ----------- | |
|
| 25 | -| `sonar.token` | Token used by the scanner to authenticate to the SonarCloud server. <br />Replaces `sonar.login` and `sonar.password` properties which are deprecated. | |
|
| 26 | -| `sonar.host.url` | https://sonar.bappartners.com/ . The URL of the SonarCloud server | |
|
| 27 | -| `sonar.projectKey` | The project's unique key. Example format: `s0027.ChallengeCR_tên_repo`| |
|
| 28 | -| `sonar.projectName` | Name of the project that will be displayed on the web interface. Example format: `s0027.ChallengeCR_tên_repo`| |
|
| 29 | -| `sonar.sources` | Analysis baseline for main source code (non-test code) in the project.| |
|
| 30 | -| `sonar.tests` | Analysis baseline for test code in the project.| |
|
| 31 | -| `sonar.sourceEncoding` | Encoding of the source files. For example, `UTF-8`, `MacRoman`, `Shift_JIS`. The list of available encodings depends on your JVM.| |
|
| 32 | -| `sonar.exclusions` | A setting used to specify file paths that you want to exclude from the SonarQube analysis process | |
|
| 33 | - |
|
| 34 | - Please visit the [official documentation of Analysis parameters](https://docs.sonarsource.com/sonarcloud/advanced-setup/analysis-parameters/) for more details. |
|
| 35 | - |
|
| 36 | - |
|
| 37 | -- Setting configuration in a file |
|
| 38 | - - Maven Java project: `pom.xml` |
|
| 39 | - - Gradle Java project: `build.gradle` |
|
| 40 | - - Ant Java project: `build.xml` |
|
| 41 | - - Other CI-based analysis: `sonar-project.properties` |
|
| 42 | - - Automatic analysis: `.sonarcloud.properties` |
|
| 43 | - |
|
| 44 | -- Setting configuration on the command line |
|
| 45 | - - For CI-based analysis (not automatic analysis), parameters can also be set on the command line using the `-D` option indicator when launching an analysis |
|
| 46 | - |
|
| 47 | -### Execute the Scanner for Maven |
|
| 48 | - Running a SonarQube analysis with Maven is straighforward. You just need to run the following command in your project's folder. |
|
| 49 | - |
|
| 50 | - ```bash |
|
| 51 | - mvn clean verify sonar:sonar \ |
|
| 52 | - -Dsonar.projectKey=test1 \ |
|
| 53 | - -Dsonar.host.url=https://sonar.bappartners.com \ |
|
| 54 | - -Dsonar.login=sqp_a8f356df86c4c1660db14aa849bc1a829aaa3e42 |
|
| 55 | - ``` |
|
| 56 | - |
|
| 57 | - Please visit the [official documentation of the Scanner for Maven](https://docs.sonarsource.com/sonarqube/9.9/analyzing-source-code/scanners/sonarscanner-for-maven/) for more details. |
|
| 58 | - |
|
| 59 | -### Execute the Scanner for Gradle |
|
| 60 | - |
|
| 61 | -1/ Running an analysis with Gradle is straighforward. You just need to declare the `org.sonarqube` plugin in your `build.gradle` file: |
|
| 62 | - |
|
| 63 | -``` |
|
| 64 | -plugins { |
|
| 65 | - id "org.sonarqube" version "3.5.0.2730" |
|
| 66 | -} |
|
| 67 | -``` |
|
| 68 | - |
|
| 69 | -2/ run the following command: |
|
| 70 | - |
|
| 71 | -```bash |
|
| 72 | -./gradlew sonar \ |
|
| 73 | - -Dsonar.projectKey=test1 \ |
|
| 74 | - -Dsonar.host.url=https://sonar.bappartners.com \ |
|
| 75 | - -Dsonar.login=sqp_a8f356df86c4c1660db14aa849bc1a829aaa3e42 |
|
| 76 | -``` |
|
| 77 | - |
|
| 78 | -### Other (for JS, TS, Go, Python, PHP, ...) |
|
| 79 | -1/ Download and unzip the Scanner for Linux |
|
| 80 | - |
|
| 81 | -- https://docs.sonarsource.com/sonarcloud/advanced-setup/ci-based-analysis/sonarscanner-cli/ |
|
| 82 | - |
|
| 83 | -2/ Execute the Scanner |
|
| 84 | - |
|
| 85 | -```bash |
|
| 86 | -sonar-scanner \ |
|
| 87 | - -Dsonar.projectKey=test1 \ |
|
| 88 | - -Dsonar.sources=. \ |
|
| 89 | - -Dsonar.host.url=https://sonar.bappartners.com \ |
|
| 90 | - -Dsonar.login=sqp_a8f356df86c4c1660db14aa849bc1a829aaa3e42 |
|
| 91 | -``` |
|
| 92 | - |
|
| 93 | -Please visit the [official documentation of the Scanner](https://docs.sonarsource.com/sonarqube/9.9/analyzing-source-code/scanners/sonarscanner/) for more details. |
|
| 94 | - |
|
| 95 | -### Scanner .NET Core Global Tool |
|
| 96 | - |
|
| 97 | -``` |
|
| 98 | -dotnet tool install --global dotnet-sonarscanner |
|
| 99 | -``` |
|
| 100 | - |
|
| 101 | -``` |
|
| 102 | -dotnet sonarscanner begin /k:"test1" /d:sonar.host.url="https://sonar.bappartners.com" /d:sonar.login="sqp_a8f356df86c4c1660db14aa849bc1a829aaa3e42" |
|
| 103 | -dotnet build |
|
| 104 | -dotnet sonarscanner end /d:sonar.login="sqp_a8f356df86c4c1660db14aa849bc1a829aaa3e42" |
|
| 105 | -``` |
|
| 106 | - |
|
| 107 | -### Execute the Scanner for Flutter |
|
| 108 | - |
|
| 109 | -- Sonar Server need to install SonarQube plugin for Flutter/Dart: https://github.com/insideapp-oss/sonar-flutter |
|
| 110 | - |
|
| 111 | -- Create `sonar-project.properties` file |
|
| 112 | -``` |
|
| 113 | -# Project identification |
|
| 114 | -sonar.projectKey=tcu.knock-fe-user |
|
| 115 | -sonar.projectVersion=1.0 |
|
| 116 | -sonar.host.url=http://localhost:9000 |
|
| 117 | -sonar.login=sqp_aae237585c0c1995591c82faae02c619eae1dc94 |
|
| 118 | - |
|
| 119 | -# Source code location. |
|
| 120 | -# Path is relative to the sonar-project.properties file. Defaults to . |
|
| 121 | -# Use commas to specify more than one file/folder. |
|
| 122 | -# It is good practice to add pubspec.yaml to the sources as the analyzer |
|
| 123 | -# may produce warnings for this file as well. |
|
| 124 | -sonar.sources=lib,pubspec.yaml |
|
| 125 | -#sonar.tests=test |
|
| 126 | - |
|
| 127 | -# Encoding of the source code. Default is default system encoding. |
|
| 128 | -sonar.sourceEncoding=UTF-8 |
|
| 129 | - |
|
| 130 | -# Analyzer mode |
|
| 131 | -# Can be: |
|
| 132 | -# - DETECT (attempt to detect automatically) - default |
|
| 133 | -# - MANUAL (an existing report needs to be provided) |
|
| 134 | -# - FLUTTER (flutter analyze) |
|
| 135 | -# - DART (dart analyze) |
|
| 136 | -# - DARTANALYZER (dartanalyzer) |
|
| 137 | -# sonar.dart.analyzer.mode= |
|
| 138 | - |
|
| 139 | -# Allows reuse of an existing analyzer report when mode is MANUAL |
|
| 140 | -# sonar.dart.analyzer.report.path= |
|
| 141 | - |
|
| 142 | -# Analyzer report output mode |
|
| 143 | -# Can be: |
|
| 144 | -# - DETECT (attempt to detect automatically, requires Dart SDK on the PATH) - default |
|
| 145 | -# - MACHINE (a new machine readable output that is available for Dart 2.12+) |
|
| 146 | -# - LEGACY (attempts to parse human readable output from dart/flutter) - default |
|
| 147 | -# sonar.dart.analyzer.report.mode= |
|
| 148 | -``` |
|
| 149 | - |
|
| 150 | -- Run the analysis and publish to the SonarQube server |
|
| 151 | -```bash |
|
| 152 | -# Download dependencies |
|
| 153 | -flutter pub get |
|
| 154 | -# Run tests with User feedback (in case some test are failing) |
|
| 155 | -#flutter test |
|
| 156 | -# Run tests without user feedback regeneration tests.output and coverage/lcov.info |
|
| 157 | -#flutter test --machine --coverage > tests.output |
|
| 158 | - |
|
| 159 | -# Run the analysis and publish to the SonarQube server |
|
| 160 | -sonar-scanner |
|
| 161 | -``` |
|
| 162 | ----- |
|
| 163 | - |
|
| 164 | -## Analyze your project with GitLab CI |
|
| 165 | -### MAVEN |
|
| 166 | - |
|
| 167 | -**1/ Add the following to your `pom.xml` file** |
|
| 168 | -``` |
|
| 169 | -<properties> |
|
| 170 | - <sonar.qualitygate.wait>true</sonar.qualitygate.wait> |
|
| 171 | -</properties> |
|
| 172 | -``` |
|
| 173 | - |
|
| 174 | - |
|
| 175 | -**2/ Add environment variables** |
|
| 176 | - |
|
| 177 | -2.1/ Define the SonarQube Token environment variable. |
|
| 178 | - |
|
| 179 | -- In GitLab, go to `Settings > CI/CD > Variables` to add the following variable and make sure it is available for your project: |
|
| 180 | -- In the Key field, enter `SONAR_TOKEN` |
|
| 181 | -- In the Value field, enter an existing token, or a newly generated one: [Generate a token](https://sonar.bappartners.com/account/security) |
|
| 182 | -- Uncheck the Protect Variable checkbox. |
|
| 183 | -- Check the Mask Variable checkbox. |
|
| 184 | - |
|
| 185 | -2.2/Define the SonarQube URL environment variable. |
|
| 186 | - |
|
| 187 | -Still in `Settings > CI/CD > Variables` add a new variable and make sure it is available for your project: |
|
| 188 | -- In the Key field, enter `SONAR_HOST_URL` |
|
| 189 | -- In the Value field, enter https://sonar.bappartners.com |
|
| 190 | -- Uncheck the Protect Variable checkbox. |
|
| 191 | -- Leave the Mask Variable checkbox unchecked. |
|
| 192 | - |
|
| 193 | - |
|
| 194 | -3/Create or update your `.gitlab-ci.yml` file with the following content. |
|
| 195 | - |
|
| 196 | -``` |
|
| 197 | -stages: |
|
| 198 | - - analyze |
|
| 199 | -sonarqube-check: |
|
| 200 | - stage: analyze |
|
| 201 | - image: maven:3.6.3-jdk-11 |
|
| 202 | - variables: |
|
| 203 | - SONAR_USER_HOME: "${CI_PROJECT_DIR}/.sonar" # Defines the location of the analysis task cache |
|
| 204 | - GIT_DEPTH: "0" # Tells git to fetch all the branches of the project, required by the analysis task |
|
| 205 | - cache: |
|
| 206 | - key: "${CI_JOB_NAME}" |
|
| 207 | - paths: |
|
| 208 | - - .sonar/cache |
|
| 209 | - script: |
|
| 210 | - - mvn verify sonar:sonar -Dsonar.projectKey=test1 |
|
| 211 | - rules: |
|
| 212 | - - if: $CI_PIPELINE_SOURCE == "merge_request_event" |
|
| 213 | - when: manual |
|
| 214 | - - if: '$CI_PIPELINE_SOURCE == "schedule" && $CI_COMMIT_BRANCH == "develop"' |
|
| 215 | - allow_failure: true |
|
| 216 | - tags: |
|
| 217 | - - sonar-scanner |
|
| 218 | -``` |
|
| 219 | - |
|
| 220 | -### gradle |
|
| 221 | - |
|
| 222 | -1/ Add the following to your `build.gradle` file |
|
| 223 | - |
|
| 224 | -``` |
|
| 225 | -plugins { |
|
| 226 | - id "org.sonarqube" version "3.5.0.2730" |
|
| 227 | -} |
|
| 228 | - |
|
| 229 | -sonar { |
|
| 230 | - properties { |
|
| 231 | - property "sonar.projectKey", "test1" |
|
| 232 | - property "sonar.qualitygate.wait", true |
|
| 233 | - } |
|
| 234 | -} |
|
| 235 | -``` |
|
| 236 | - |
|
| 237 | -Example: |
|
| 238 | -``` |
|
| 239 | -// SonarQube |
|
| 240 | -sonar { |
|
| 241 | - properties { |
|
| 242 | - property 'sonar.sourceEncoding', 'UTF-8' |
|
| 243 | - property 'sonar.language', 'java' |
|
| 244 | - property 'sonar.java.binaries', '**/build/classes' |
|
| 245 | - property 'sonar.exclusions', '**/com/honda/rd/**,**/ext/preevisionadapter/**' |
|
| 246 | - property 'sonar.issue.ignore.allfile', 'e1' |
|
| 247 | - property 'sonar.issue.ignore.allfile.e1.fileRegexp', '@Test' |
|
| 248 | - property 'sonar.issue.ignore.allfile', 'e2' |
|
| 249 | - property 'sonar.issue.ignore.allfile.e2.fileRegexp', '@ParameterizedTest' |
|
| 250 | - property 'sonar.junit.reportPaths', 'build/test-results/aggregate' |
|
| 251 | - property 'sonar.coverage.jacoco.xmlReportPaths', 'build/reports/jacoco/aggregate/jacocoTestReport.xml' |
|
| 252 | - property 'sonar.coverage.exclusions', '**/src/test/**' |
|
| 253 | - property 'sonar.cpd.exclusions', '**/src/test/**' |
|
| 254 | - } |
|
| 255 | -} |
|
| 256 | -project.tasks['sonar'].dependsOn 'junit5TestReport' |
|
| 257 | -project.tasks['sonar'].dependsOn 'aggregateJacocoMerge' |
|
| 258 | -``` |
|
| 259 | - |
|
| 260 | -2/ Create or update your `.gitlab-ci.yml` file with the following content. |
|
| 261 | -``` |
|
| 262 | -stages: |
|
| 263 | - - analyze |
|
| 264 | -sonarqube-check: |
|
| 265 | - stage: analyze |
|
| 266 | - image: gradle:jre11-slim |
|
| 267 | - variables: |
|
| 268 | - SONAR_USER_HOME: "${CI_PROJECT_DIR}/.sonar" # Defines the location of the analysis task cache |
|
| 269 | - GIT_DEPTH: "0" # Tells git to fetch all the branches of the project, required by the analysis task |
|
| 270 | - cache: |
|
| 271 | - key: "${CI_JOB_NAME}" |
|
| 272 | - paths: |
|
| 273 | - - .sonar/cache |
|
| 274 | - script: gradle sonar |
|
| 275 | - rules: |
|
| 276 | - - if: $CI_PIPELINE_SOURCE == "merge_request_event" |
|
| 277 | - when: manual |
|
| 278 | - - if: '$CI_PIPELINE_SOURCE == "schedule" && $CI_COMMIT_BRANCH == "develop"' |
|
| 279 | - allow_failure: true |
|
| 280 | - tags: |
|
| 281 | - - sonar-scanner |
|
| 282 | -``` |
|
| 283 | - |
|
| 284 | -### Other (for JS, TS, Go, Python, PHP, ...) |
|
| 285 | - |
|
| 286 | -1/ Create a `sonar-project.properties` file in your repository and paste the following code |
|
| 287 | - |
|
| 288 | -``` |
|
| 289 | -# must be unique in a given SonarQube instance |
|
| 290 | -sonar.projectKey=s0168.Monocad_lambda-flask-api |
|
| 291 | -# --- optional properties --- |
|
| 292 | - |
|
| 293 | -# defaults to project key |
|
| 294 | -sonar.projectName=s0168.Monocad_lambda-flask-api |
|
| 295 | -# defaults to 'not provided' |
|
| 296 | -#sonar.projectVersion=1.0 |
|
| 297 | - |
|
| 298 | -# Path is relative to the sonar-project.properties file. Defaults to . |
|
| 299 | -# sonar.projectBaseDir=. |
|
| 300 | -# sonar.sources=./src,./resources,./web |
|
| 301 | -sonar.sources=./app |
|
| 302 | - |
|
| 303 | -# Encoding of the source code. Default is default system encoding |
|
| 304 | -sonar.sourceEncoding=UTF-8 |
|
| 305 | - |
|
| 306 | -#sonar.test.inclusions=**/*Test.js |
|
| 307 | - |
|
| 308 | -#sonar.exclusions=,**/coverage/** |
|
| 309 | - |
|
| 310 | -# Fail CI pipeline if Sonar fails. |
|
| 311 | -sonar.qualitygate.wait=true |
|
| 312 | -``` |
|
| 313 | - |
|
| 314 | -2/ Create or update your `.gitlab-ci.yml` file with the following content. |
|
| 315 | -``` |
|
| 316 | -stages: |
|
| 317 | - - analyze |
|
| 318 | -sonarqube-check: |
|
| 319 | - stage: analyze |
|
| 320 | - image: |
|
| 321 | - name: sonarsource/sonar-scanner-cli:4.8 |
|
| 322 | - entrypoint: [""] |
|
| 323 | - variables: |
|
| 324 | - SONAR_USER_HOME: "${CI_PROJECT_DIR}/.sonar" # Defines the location of the analysis task cache |
|
| 325 | - GIT_DEPTH: "0" # Tells git to fetch all the branches of the project, required by the analysis task |
|
| 326 | - cache: |
|
| 327 | - key: "${CI_JOB_NAME}" |
|
| 328 | - paths: |
|
| 329 | - - .sonar/cache |
|
| 330 | - script: |
|
| 331 | - - sonar-scanner |
|
| 332 | - rules: |
|
| 333 | - - if: $CI_PIPELINE_SOURCE == "merge_request_event" |
|
| 334 | - when: manual |
|
| 335 | - - if: $CI_PIPELINE_SOURCE == "schedule" && $CI_COMMIT_BRANCH == "develop" |
|
| 336 | - allow_failure: true |
|
| 337 | - tags: |
|
| 338 | - - sonar-scanner |
|
| 339 | -``` |
|
| 340 | - |
|
| 341 | -### NET |
|
| 342 | - |
|
| 343 | -**1/ Add environment variables** |
|
| 344 | - |
|
| 345 | -1.1/ Define the SonarQube Token environment variable. |
|
| 346 | - |
|
| 347 | -- In GitLab, go to `Settings > CI/CD > Variables` to add the following variable and make sure it is available for your project: |
|
| 348 | -- In the Key field, enter `SONAR_TOKEN` |
|
| 349 | -- In the Value field, enter an existing token, or a newly generated one: [Generate a token](https://sonar.bappartners.com/account/security) |
|
| 350 | -- Uncheck the Protect Variable checkbox. |
|
| 351 | -- Check the Mask Variable checkbox. |
|
| 352 | - |
|
| 353 | -1.2/Define the SonarQube URL environment variable. |
|
| 354 | - |
|
| 355 | -Still in `Settings > CI/CD > Variables` add a new variable and make sure it is available for your project: |
|
| 356 | -- In the Key field, enter `SONAR_HOST_URL` |
|
| 357 | -- In the Value field, enter https://sonar.bappartners.com |
|
| 358 | -- Uncheck the Protect Variable checkbox. |
|
| 359 | -- Leave the Mask Variable checkbox unchecked. |
|
| 360 | - |
|
| 361 | -2/ Create or update your `.gitlab-ci.yml` file with the following content. |
|
| 362 | -``` |
|
| 363 | -sonarqube-check: |
|
| 364 | - image: mcr.microsoft.com/dotnet/core/sdk:latest |
|
| 365 | - variables: |
|
| 366 | - SONAR_USER_HOME: "${CI_PROJECT_DIR}/.sonar" # Defines the location of the analysis task cache |
|
| 367 | - GIT_DEPTH: "0" # Tells git to fetch all the branches of the project, required by the analysis task |
|
| 368 | - cache: |
|
| 369 | - key: "${CI_JOB_NAME}" |
|
| 370 | - paths: |
|
| 371 | - - .sonar/cache |
|
| 372 | - script: |
|
| 373 | - - "apt-get update" |
|
| 374 | - - "apt-get install --yes openjdk-11-jre" |
|
| 375 | - - "dotnet tool install --global dotnet-sonarscanner" |
|
| 376 | - - "export PATH=\"$PATH:$HOME/.dotnet/tools\"" |
|
| 377 | - - "dotnet sonarscanner begin /k:\"s0202.meta.b2b.unity_fe\" /d:sonar.login=\"$SONAR_TOKEN\" /d:\"sonar.host.url=$SONAR_HOST_URL\" " |
|
| 378 | - - "dotnet build" |
|
| 379 | - - "dotnet sonarscanner end /d:sonar.login=\"$SONAR_TOKEN\"" |
|
| 380 | - allow_failure: true |
|
| 381 | - only: |
|
| 382 | - - merge_requests |
|
| 383 | - - staging |
|
| 384 | - - develop |
|
| 385 | -``` |
sonarqube/setting_hierachy.png
| ... | ... | Binary files a/sonarqube/setting_hierachy.png and /dev/null differ |